What Statement Best Describes What Encryption Is
It turns data into cipher text. A Encryption completely protects your data.
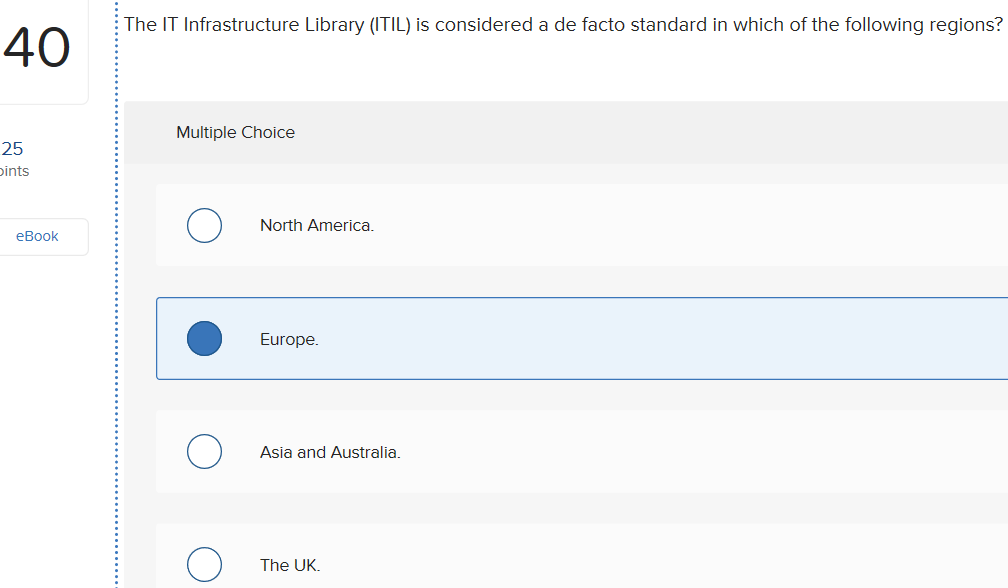
Solved Which Of The Following Best Describes What Is Meant Chegg Com
Which of the following statements describe encryption.
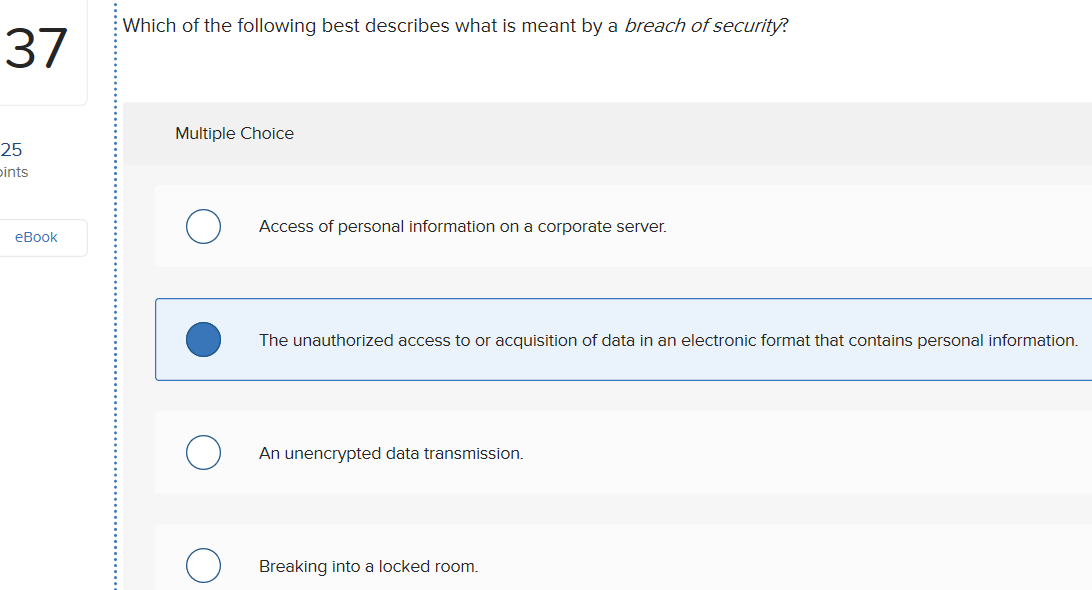
. AES is an encryption protocol and provides data confidentiality. Can be used as a signature system and a cryptosystem. Which of the following statements describe encryption.
Symmetric encryption is more efficient for bulk encryption of large amounts of data for transfer. Which statement about encryption is True about data in use. Which statement describes a distributed denial of service attack An attacker views network traffic to learn authentication credentials.
It helps secure data. It shares files with other computers. Which statement best describes configuring a NAT router to use dynamic mapping.
An encryption method in which numbers generated by an algorithm from a text string are used to verify the integrity of transmitted messages Which statement best describes hash encryption. O Encyrption hides data in plain sight. Which of the following statements best describes symmetric key encryption.
It makes data unreadable without a decryption. C Encryption only works. Section 4 Basic Cryptography Which two statements best describe the impact of cryptography on security investigations.
Which of the following statements best describes the primary purpose for using one-way encryption of user passwords within a system. A cryptographic security mechanism that uses public and private keys to encrypt and decrypt data. 9 The following statement best describes encryption on the internet.
It is easily seen but difficult to interpret. An attacker builds a botnet comprised of zombies. DH Diffie-Hellman is an algorithm that is used for key exchange.
A cryptographic security mechanism that uses the same key for both encryption and decryption. With the increased legitimate usage of HTTPS traffic attackers have taken advantage of this blind spot to launch attacks over HTTPS more than ever before. It turns data into cipher text.
Why is network security important. Cryptographic attacks can be used to find a weakness in the cryptographic algorithms. Encryption is a technical and data safeguard that converts clear text in a random set of characters.
Which statement best describes asymmetric-key encryption. Search for an answer or ask Weegy. Check all of the boxes that apply.
Check all of the boxes. The following statement best describes encryption on. B Encryption assists in an overall security program.
One computer accepts data packets based on the MAC address of another computer. Which of the following statements best describes network security. The organization will need as many registered IP addresses as it has computers that need Internet access.
A method used to encrypt confidential data. It makes data unreadable without a decryption key. An attacker sends an enormous quantity of data that a server cannot handle.
Data should always be kept encrypted since modern CPUs are fully capable of operating directly on. The most secure email message authenticity and confidentiality is provided by signing the message using the senders private key and encrypting the message using the receivers public key. Asymmetric encryption is used for authentication non-repudiation and key agreement and exchange.
It makes using a computer difficult. Check all of the boxes that apply. Encryption is BEST described as a.
Hypertext Transfer Protocol HTTP. Which statement best describes encryption. Network security protects individuals privacy.
The art of transferring handwritten signatures to electronic media. Symmetric encryption is very fast and used for bulk encryption of large amounts of data. Allows the recipient of data to prove the source and integrity of data.
An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message Which term is used to describe an application that installs hidden services on a system that enables the attacker to monitor and control the operation of the system.
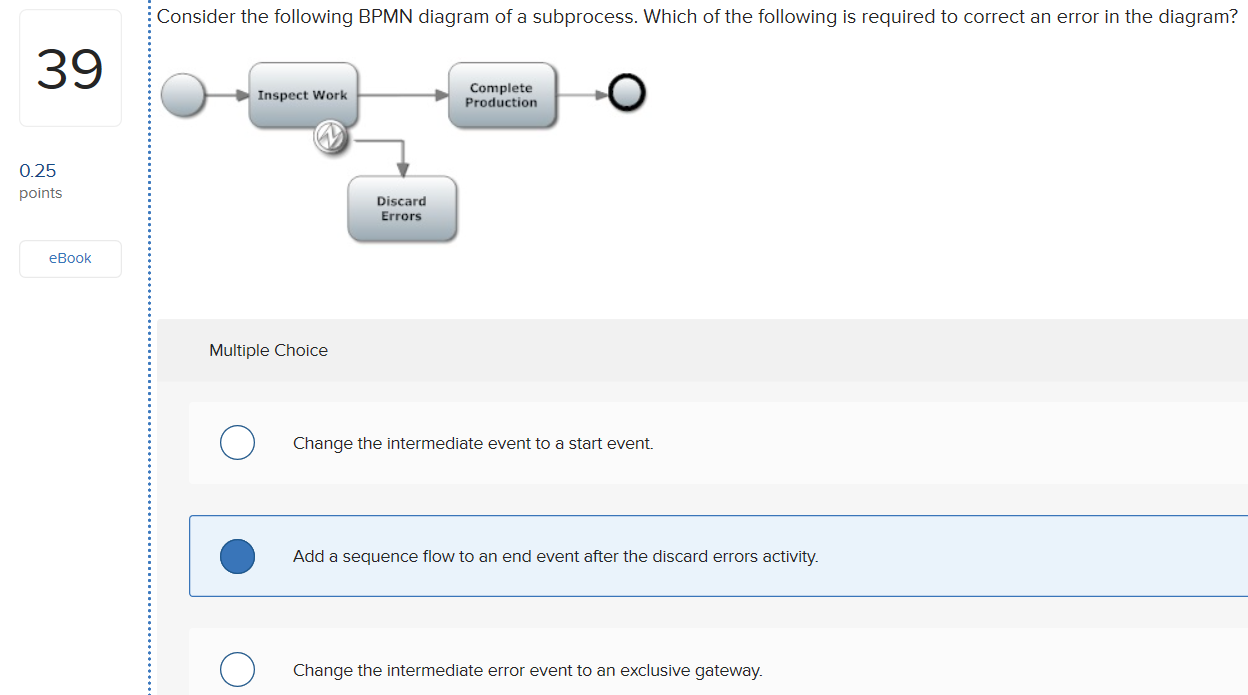
Solved Which Of The Following Best Describes What Is Meant Chegg Com

Which Of The Following Best Describes Aes Skillset

Solved Which Of The Following Best Describes What Is Meant Chegg Com
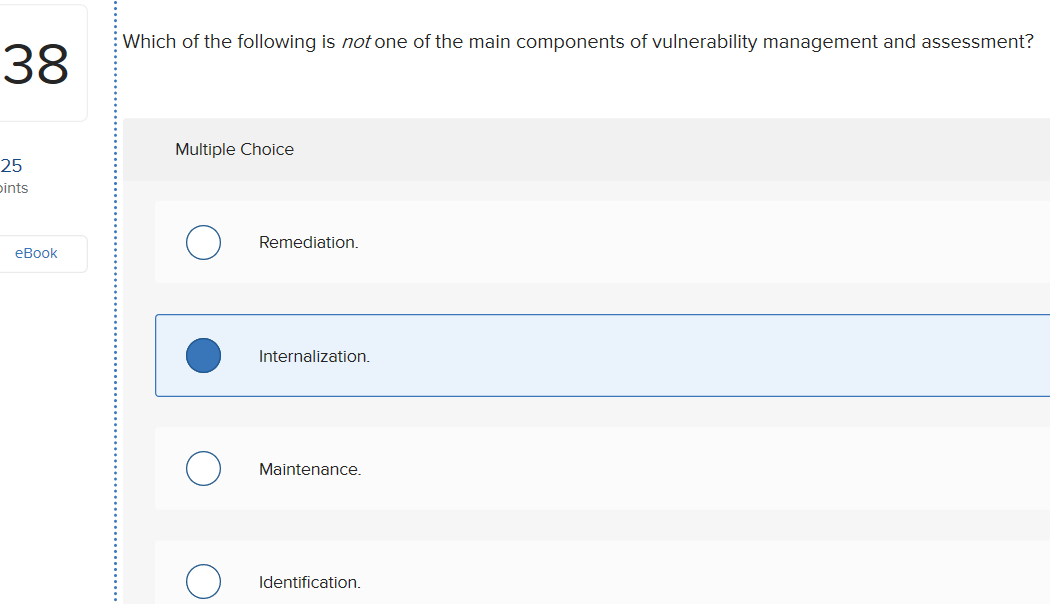
Solved Which Of The Following Best Describes What Is Meant Chegg Com
Comments
Post a Comment